DC-labels
Exercise 1: Privacy labels
Verify the following privacy assertions (involving ⊑C) in
COWL. Implement the assertions using COWL.privacyLabel and calling subsumes
on it. Justify why the assertions hold or why they do not.
http://alice.com:8080∧http://bob.com:9090⊑Chttp://bob.com:9090http://alice.com:8080∨http://bob.com:9090⊑Chttp://bob.com:9090http://alice.com:8080⊑Chttp://bob.com:9090∧http://charlie.com:5050http://alice.com:8080⊑Chttp://bob.com:9090∨http://alice.com:8080http://bob.com:9090⊑Chttp://bob.com:9090∧http://alice.com:8080
Exercise 2: Integrity labels
Verify the following integrity assertions (involving ⊑I) in
COWL. Implement the assertions using COWL.trustLabel and calling subsumes
on it. Justify why the assertions hold or why they do not.
http://alice.com:8080∧http://bob.com:9090⊑Ihttp://bob.com:9090http://bob.com:9090⊑Ihttp://alice.com:8080∧http://bob.com:9090http://bob.com:9090⊑Ihttp://alice.com:8080∨http://bob.com:9090http://bob.com:9090∨http://alice.com:8080⊑Ihttp://alice.com:8080∨http://bob.com:9090∨http://charlie.com:5050
Exercise 3: Privileges
As the exercise above, verify the following assertions using COWL. Implement
them by creating user-minted privileges and manipulating COWL.privacyLabel and
COWL.privileges. We note Label() as the security
level denoting public data. Justify why the assertions hold or why they do not.
We assume two user-minted privileges p1 and p2, and the labels obtained from
them as l1 and l2, respectively.
l1∧l2⊑Cp2l2l1∧l2⊑Cp1l2l1⊑Cp1Label()l1∨l2⊑Cp1Label()l1∧l2⊑Cp1∧p2Label()l1∧l2⊑Cp2l1∨l2
COWL
Exercise 4: Charlie gets into the scene
In this exercise, you are asked to extend the code example which involves Alice and Bob iframes to consider a new actor: Charlie. More precisely, you need to extend the source code in
WebSiteA/iframeAlice2.htmlWebSiteB/iframeBob2.html
Charlie is running in the origin http://charlie.com:5050 (you can install a
local web server for Charlie as you did for Alice and Bob).
The scenario is as follows. Bob's iframe embeds Charlie web page in an iframe as shown in the picture.
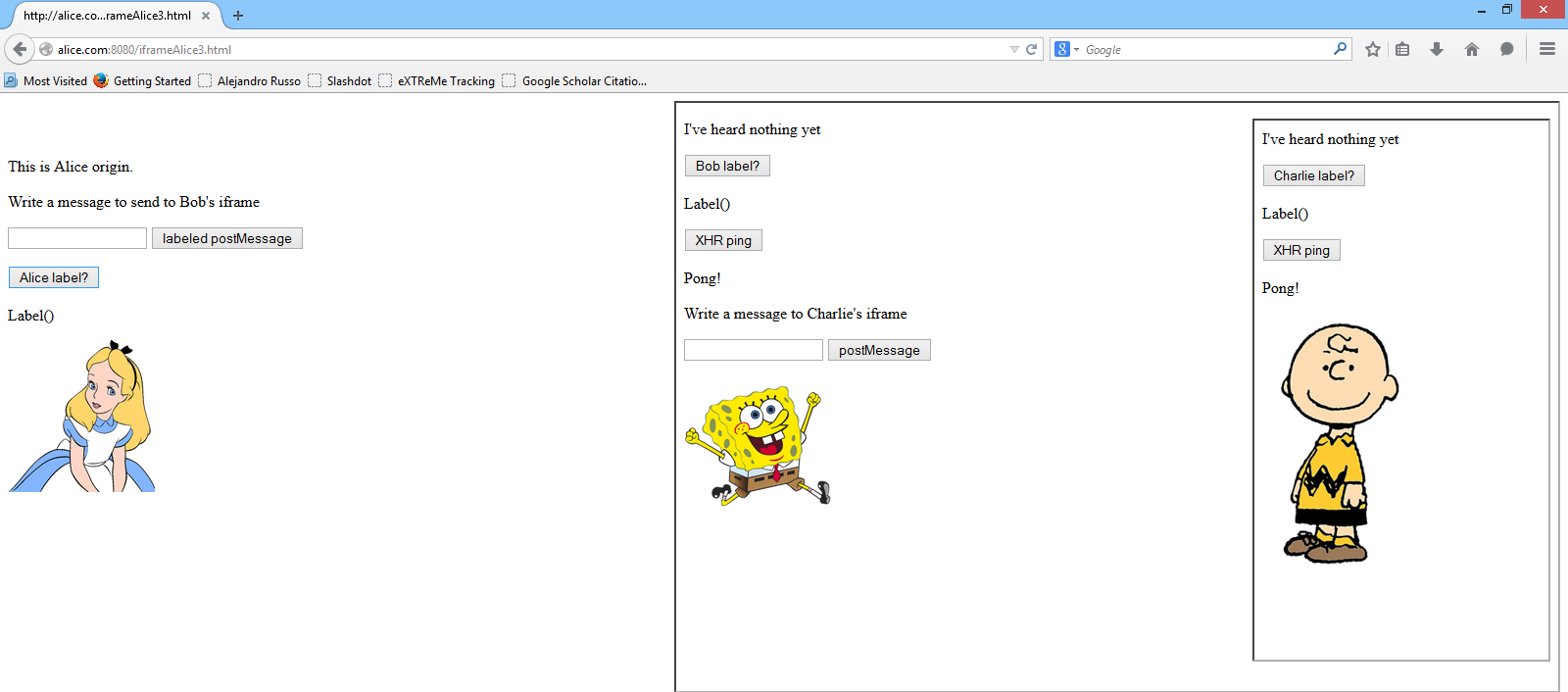
Charlie's web page works similarly as Bob's except that it queries Charlie's browsing context label and pings Charlie's server. Bob's iframe can send messages to Charlie if confidentiality is not compromised.
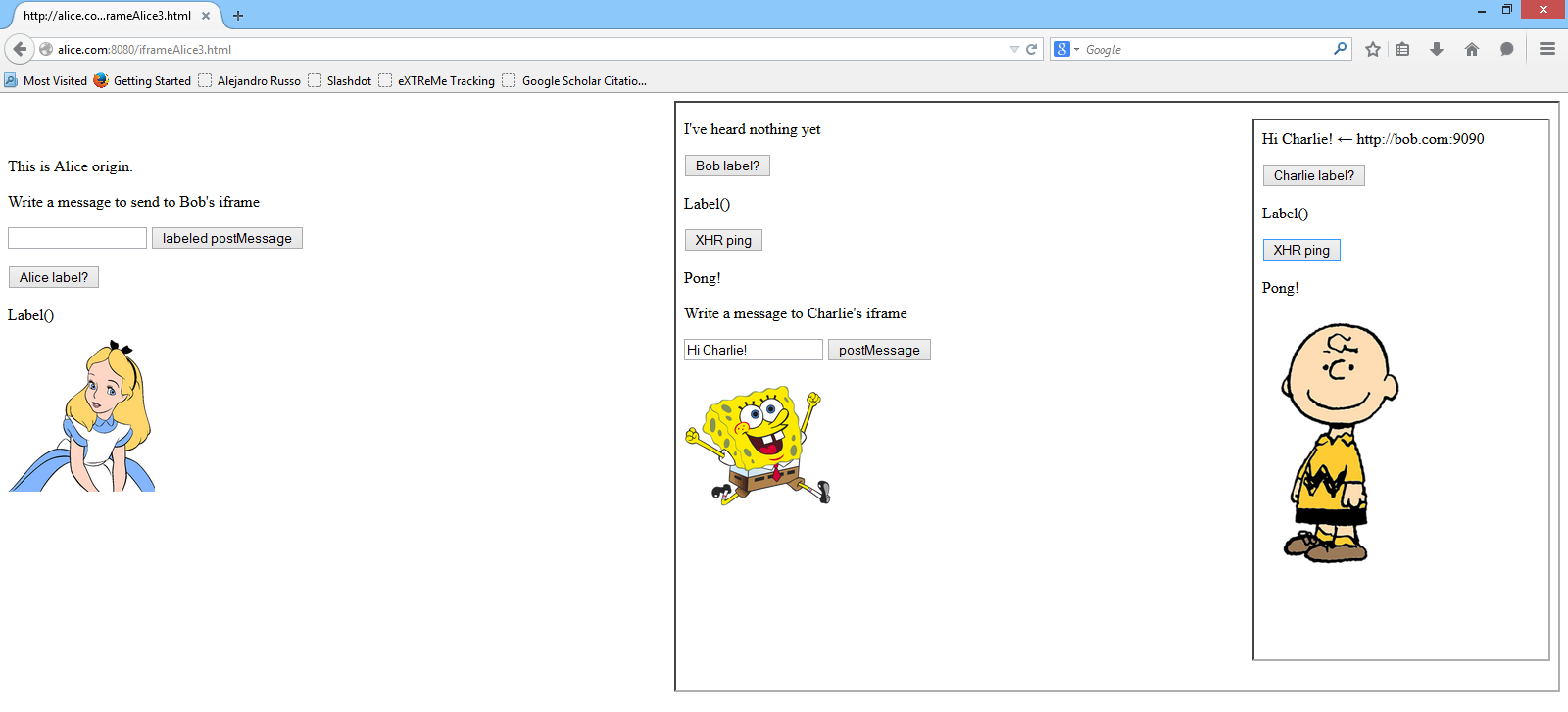
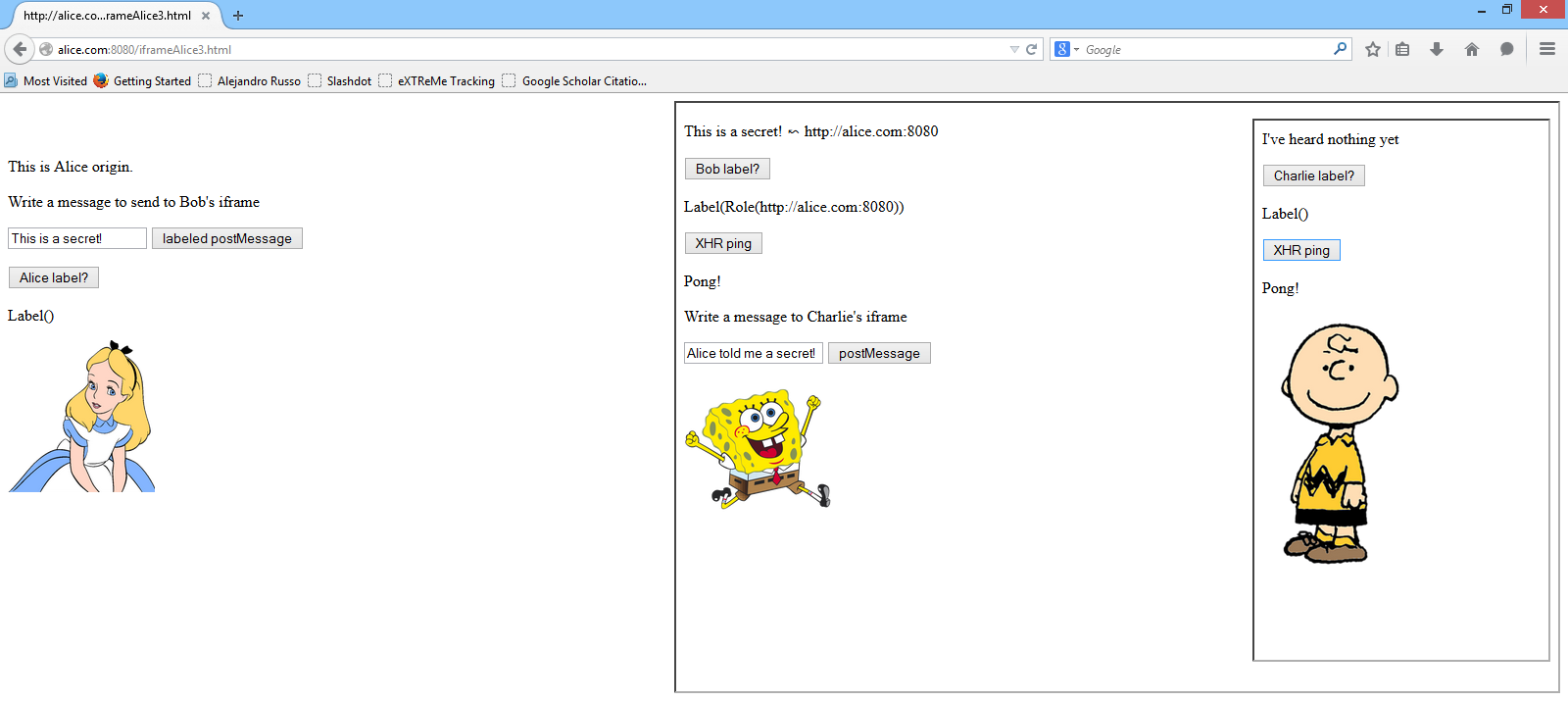
As the image above shows, Bob can send public messages to Charlie (observe Bob's
label as Label()) and Charlie can still ping his server. However, if Alice
sends a secret message to Bob, then he lost any communication capabilities with
Charlie, and thus Charlie can no longer receives messages from him.
Your code should include the following files:
WebSiteA/iframeAlice3.html, where Alice creates an iframe to include Bob's page.WebSiteB/iframeBob3.html, where Bob creates an iframe to include Charlie's page.WebSiteC/iframeCharlie.html, where Charlie implements his web page.
Exercise 5: Labeled XHR
Implement the idea of Labeled XHR presented in the class room. More specifically, provide the function which takes a URL where to perform a XHR request and returns a labeled blob labeled with the corresponding origin. For example,
labeledXHR("http://alice.com:8080/index.html");
should trigger a XHR request to the origin http://alice.com:8080, and it
should send the result as a labeled blob in a postMessage. Importantly,
labeledXHR should not raise the browsing context label.
Taint analysis
Exercise 6: Bypassing taint analysis
In the course, we mentioned that taint analysis is not effective for malicious code. The reason for that is the power that the attacker has to bypass the analysis by exploiting the control flow constructs.
In this exercise, you are the attacker who provides malicious code. Your goal is
to deploy the function bypass which bypasses the taint analysis. More
specifically, you should implement the following function in Python:
def bypass(some_string): ... end
which always returns an untainted string.
Your function should not be responsible to raise an alarm of the taint analysis. For instance, the following code should run without reporting any problems:
tstring = taint("This is tainted data")
# If you run tainted(tstring) in the Python prompt, you should see True
ustring = bypass(tstring)
# Now, ustring should have the same value as tstring but it is not tainted
# If you run tainted(ustring) in the Python prompt, you should see False