PRECIS: Privacy and Security in Wearable Computing Devices
Wearable and ubiquitous computing will create a wave of adoption similar to smartphones, enabling new applications in areas such as smart homes and healthcare. They collect unique information about each individual and can offer transparent authentication. However they have weak security and scatter our digital fingerprints across different services. PRECIS has the ambitious goal to address this challenge and to introduce a unifying framework for authentication in wearable computing that provides: (i) accurate and transparent authentication, (ii) rigorous privacy guarantees, even if multiple wearable devices are involved in the authentication. PRECIS is funded by the Swedish Research Council (VR).
SwissSenseSynergy
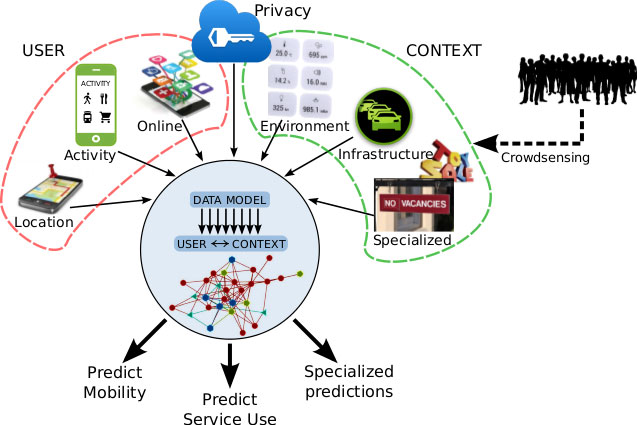
The SwissSenseSynergy project aims to bring together research from closely related fields that have recently emerged due to the proliferation of wireless computing devices. In particular, the ubiquity of smart phones as well as plans to deploy large numbers of small, local-range base stations (femto cells) creates many opportunities for synergistic computation as well as numerous privacy and security concerns for the users. The overall goal of SwissSenseSynergy is to provide a unifying framework for secure localisation and privacy-preserving location-based services. This is sure to lead to many innovations in the intersection of localisation, resource allocation, decision making, location-based services and privacy preservation. The project partners have been chosen deliberately to bring together capabilities not available at any one institution. Each partner is represented by experienced researchers in the field of wireless communications, distributed computing, simulations and experimental evaluations, statistics as well as security and privacy. Partners in this project are: University of Bern, Chalmers University of Technology, University of Geneva and SUPSI. The project is funded by the SNSF. More info about the project are available here.
BEAT: Biometric Evaluation and Testing

Identity management using biometrics is deployed in a growing number of applications ranging from identification platforms (e.g. biometric passports) to access control systems for border checks or banking transactions. Unfortunately, the reliability of these technologies remains difficult to compare. There are no european-wide standards for evaluating their accuracy, their robustness to attacks or their privacy preservation strength. BEAT will fill this gap by building an online and open platform to transparently evaluate biometric systems, designing protocols and tools for vulnerability analysis and developing standardization documents for Common Criteria evaluations. The planned impact is three-fold: the reliability of biometric systems becomes standardized and comparable, potentially leading to a meaningful increase in their performance; technology transfer from research to companies becomes easier with the use of an interoperable framework; authorities and decision-makers become more informed about the progress made in biometrics as results impact standards. Chalmers is focusing pn privacy-preservation aspects in biometric authentication. BEAT is funded by the EU (FP7) more info about this project are available here.
Secure, Private and Efficient Healthcare with Wearable Computing
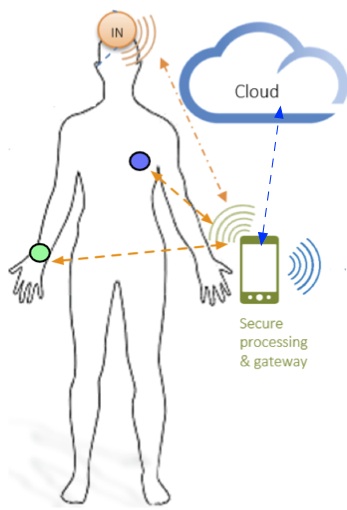
Wearable devices create exciting opportunities for home monitoring of chronic/elderly patients and reduce the length/cost of hospitalization. However, the very same devices have weak security and scatter sensitive data. We envision that via advanced wireless technologies, wearable health monitoring devices can transmit data directly to a healthcare service provider (cloud), and receive commands from the cloud for device authentication, privacy protection and personalized healthcare treatments. The system can be very simple in its architecture, yet extremely powerful in its functionality. This project shall study the architecture and data analytics for such a system and focus on: (i) employing statistical methods and machine learning techniques to the collected data to extract its medical meaning; (ii) investigate efficient and privacy-preserving: authentication protocols and verifiable outsourcing/delegation of computations to the cloud. We shall approach this problem from a cross-disciplinary perspective and use advances from cryptography, and machine learning. We will employ a prototype system, called Cloud Sense for Health, to gather substantial healthcare data to support research in medicine and statistical learning. The partners of this project are: Chalmers University of Technology and Harvard University. The project is funded by STINT.
PriSecIoT: Security and Privacy for the Future Internet of Things

The Internet of Things (IoT) is a pillar of the future Internet. Recent advances in miniaturization, battery life, energy harvesting, hardware costs and transmission protocols have brought even closer the IoT vision of pervasively connecting everything. While single applications in the context of IoT are getting more common, they provide mostly partial solutions to the ``Intranet of Things" rather than the Internet of Things. To guarantee the sustainable development of the IoT and promote it as a publicly accepted and implemented paradigm we need to overcome the current fragmentation and limitation of partial solutions towards a true ``Internet of Things". PriSecIoT has as goal to set a roadmap for a unified framework for a secure and privacy-preserving IoT that scales in multiple heterogeneous devices. The partners of this project are: Chalmers University of Technology and ETHZ. The project is funded by Västra Götalansregionen (MoRE fellowship) and EU (FP7).
SEAFRONT: Secure, Private, Fast and Reliable Wireless Communications
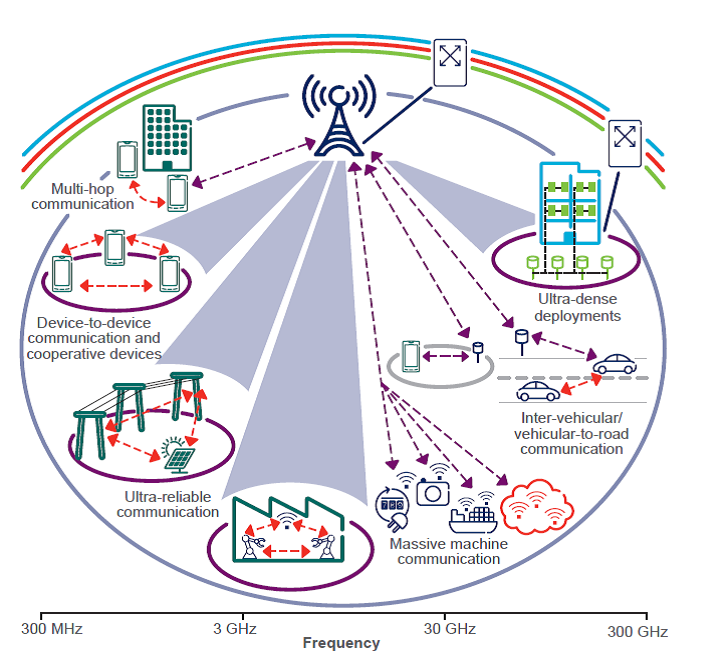
The next generation of wireless systems is expected to turn wireless connectivity into a true commodity ``...for anything that may benefit from being connected...'', ranging from tiny wearable sensors to vehicles and drones. A successful implementation of this internet-of-things (IoT) vision calls for a wireless communication system that: (i) is able to support a much larger number of connected devices, (ii) is able to fulfil much more stringent requirements on latency and reliability, and (iii) offers more sophisticated privacy-preserving authentication and security mechanisms. The introduction of future services based on machine-type communication, such as intelligent transportation, augmented reality, remote health care, smart metering, and industrial automation heavily rely on the availability of such a wireless communication system. Indeed all these services require a reliable and low-latency wireless connectivity with strong security and privacy guarantees. The central objective of SEAFRONT is to determine the minimum end-to-end latency that can be guaranteed in wireless communication links where short data packets need to be transmitted with high requirements on reliability, security, and privacy. This is a collaborative project at Chalmers between the Department of Computer Science and Engineering and the Department of Signals and Systems funded by Chalmers ICT Areas of Advance.
Large-scale private adaptive experiments for drug discovery
This project is part of a larger effort to develop algorithms for large-scale experiment design for the problem of automated drug development. Drug compounds are described by complicated models, and their effectiveness can only be ascertained through laboratory, animal and human testing. A large number of drugs and parameters need to be measured in the and it is impossible to test them all. Existing data about different drugs and their effects may also create privacy issues. These may be due to patient privacy or due to the value attached to expensively collected data. This project will primarily implement algorithms for large-scale experiment design, test them and benchmark them. A second goal is to develop an open framework for communicating experimental specifications, data, results and inferred models. In particular, we would like to be able to interface with collaborative databases such as the open toxicity database. This is a collaborative project at Chalmers between the Department of Computer Science and Engineering and the Department of Mathematical Sciences funded by Chalmers ICT Areas of Advance.
Authentication in Constrained Settings
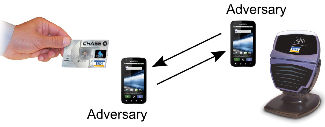
Communication technologies have changed the way we do business, travel, manage our personal lives and communicate with our friends. In many cases, this crucially depends on accurate and reliable authentication. We need to get authenticated in order to get access to restricted services and/or places. The overall goal of the project is to develop privacy-preserving authentication mechanisms for noisy, constrained and hostile environments that strike an optimal balance of reliable (accurate) authentication, privacy-preservation and resource consumption. Authentication is especially challenging when it appears under constrained settings due to: (i) privacy issues, (ii) noisy conditions, and (iii) resource limits. Privacy-preservation is essential for the protection of sensitive information (i.e. diseases, location, nationality). Noisy conditions refer to physical noise in the communication channel that may lead to modification of the transmitted information, or natural variability due to the authentication medium (e.g. fingerprint scans). Resource constraints refer to limited device power/abilities (i.e. sensors, RFID tags). The project is funded by Chalmers ICT Areas of Advance.
Cross-layer Authentication Protocols for Wireless Networks
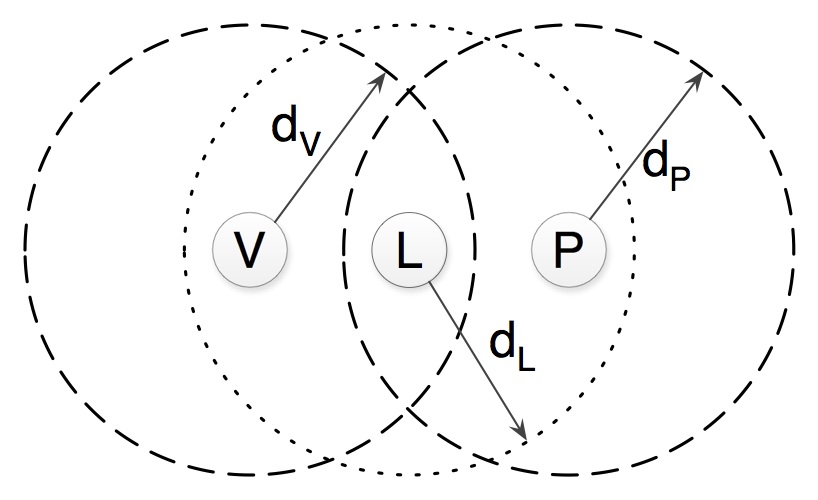
The goal of this project is to explore practical security approaches for cross-layer authentication by employing mechanisms operating at the physical layer of wireless communication, in combination with conventional cryptography. This combination shall enable new authentication protocols for a variety of low-resource wireless devices. Cross-layer protocol design could solve important security challenges in ad-hoc wireless environments that cannot effectively be solved only with conventional cryptography, such as relay-resistant authentication. Cross-layer security protocol design has the potential to bring about benefits in wireless networks where computational and power resources are constrained, or where communication needs to be made robust for purposes of reliability and fault tolerance. This project will focus on the design and implementation of efficient authentication mechanisms, specifically distance-bounding protocols, that can be employed to verify the physical proximity of the party that is authenticated in wireless ad-hoc networks, such as wireless sensor networks and NFC-enabled mobile device communication. The partners of this project are: Chalmers University of Technology and City University of Hong Kong. The project is funded by STINT. More info about a workshop organised and funded by this STINT project is available here.
CRYPTACUS: CRYPTAnalysis of ubiquitous CompUting Systems

Recent technological advances in hardware and software have irrevocably affected the classical picture of computing systems. Today, these no longer consist only of connected servers, but involve a wide range of pervasive and embedded devices, leading to the concept of "ubiquitous computing systems". The objective of the Action is to improve and adapt the existent cryptanalysis methodologies and tools to the ubiquitous computing framework. Cryptanalysis, which is the assessment of theoretical and practical cryptographic mechanisms designed to ensure security and privacy, will be implemented along four axes: cryptographic models, cryptanalysis of building blocks, hardware and software security engineering, and security assessment of real-world systems. The project is funded by the EU Cost. More info about the project is available here.
PPIDR: Privacy Preserving Intrusion Detection and Response In Wireless Communications

Intrusion detection techniques can safeguard wireless communications and reduce the impact of malicious activities that cannot be prevented via cryptographic or other security measures. The goal of PPIDR was to investigate intrusion detection and response techniques in wireless ad hoc networks and especially WSN and RFID systems. In wireless ad hoc networks, the malicious status of nodes is uncertain. The second goal was to respond to suspected intrusions in a way that optimally balances the promptness of warnings, the reliability of decisions and the network performance. The third goal was to extend intrusion detection and response mechanisms to the adversarial case: i.e. the case where the attacker is behaving in a rational manner in order to more effectively evade it. Recent advances in this area make this a particularly interesting avenue of investigation. Our research focused on making such algorithms practical and evaluating them in various traffic conditions and types of attacks. Because of the potential privacy implications of monitoring large numbers of users and network nodes our research will also devote considerable effort to safeguard the privacy of the involved parties and develop privacy-preserving intrusion detection and response systems, based on recent developments in the areas of privacy-preserving data mining, inference and database systems. This project was funded by a Marie Curie IE Fellowship (EU FP7) and was performed at EPFL. More info about the project is available here.